¶ How to separate prefixes by threshold
¶ Purpose of this Wiki
Demonstrate how to register and organize prefixes in the anti-DDoS module, associating each group of IPs to a specific threshold, with the objective of applying more appropriate rules for detecting and mitigating attacks according to the type of use or critical nature of each block.
¶ Accessing the module
Through the left side menu of Made4flow, enter the anti-DDos module:
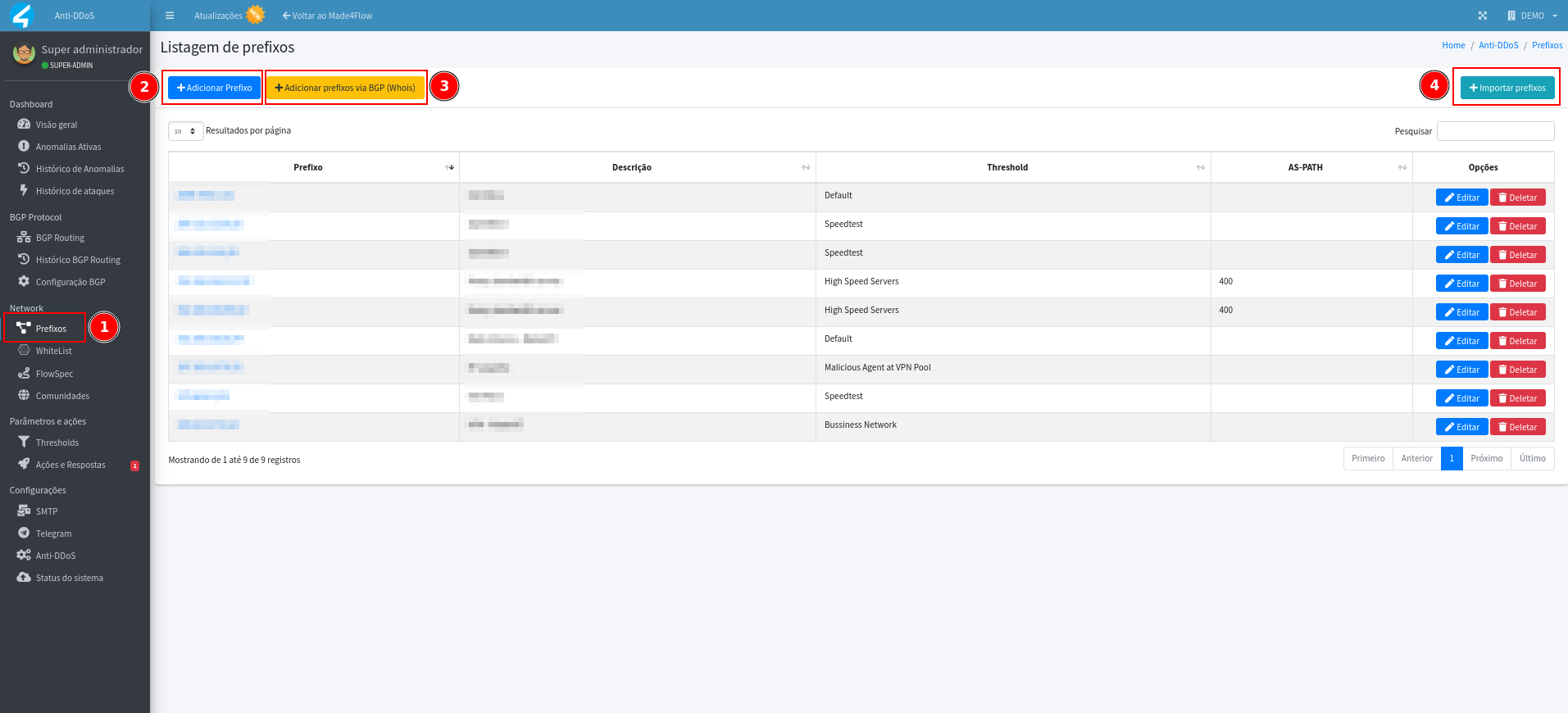
¶ Prefix registration
In the Prefix tab, you can register manually, add via whois through the ASN, or import the prefixes already registered in Made4flow:
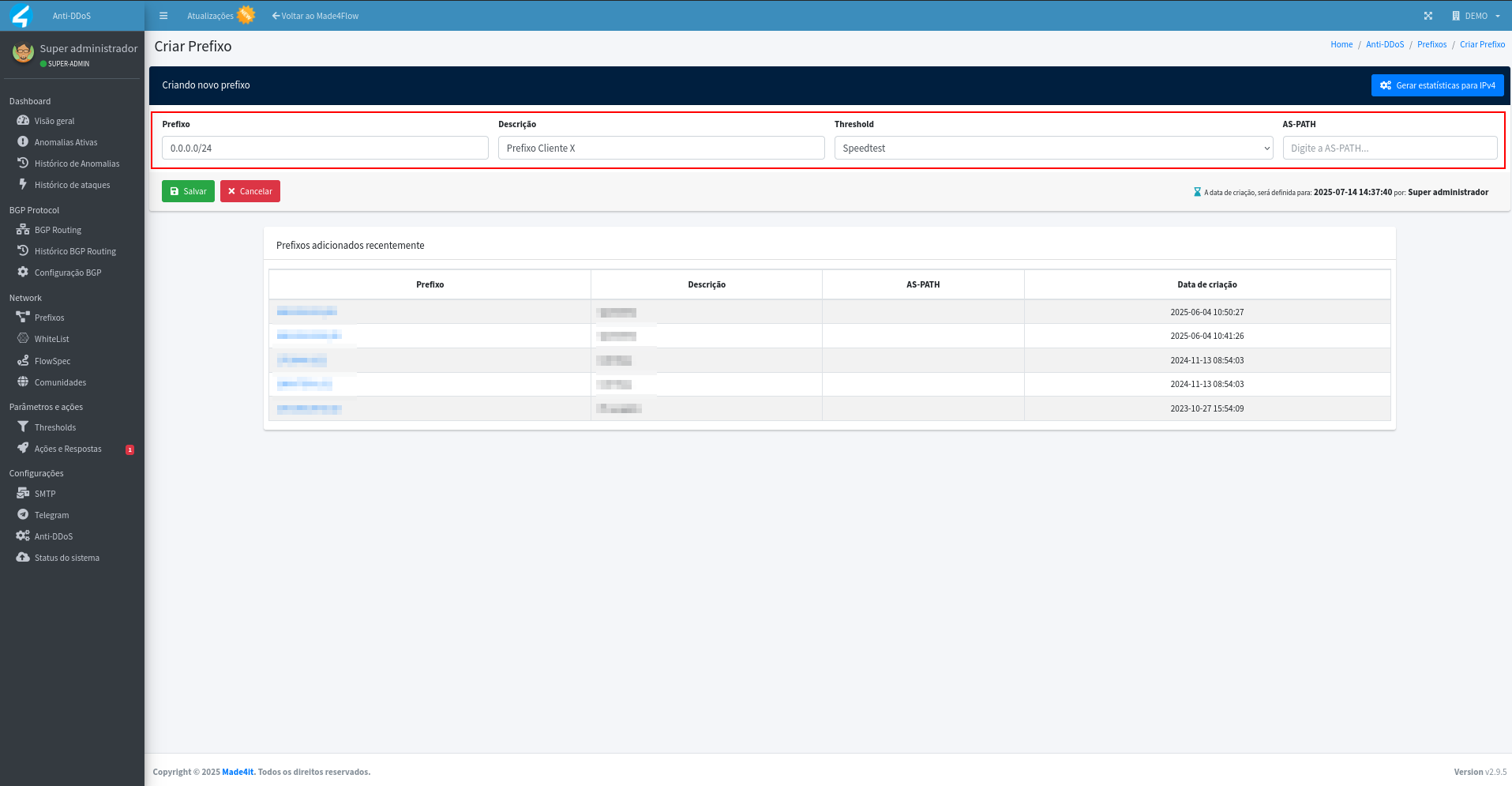
For all cases, it will be possible to select the existing thresholds that you want to associate with the prefixes that are being created or imported:
**Note: ** If there is only the Default threshold, suggestions for categorization such as ASNS Clients, Servers, CGNAT, CDN, DNS, Speedtest, and Corporate Clients can be used. If the IP blocks are organized by contracted band (e.g., 400 Mb, 600 Mb, 1 Gb plans, or 10 Gb clients), this information can also be used to further refine the segmentation. This separation makes it easier to apply thresholds with more precise rules for each traffic profile.
¶ Prefix registration fields
Below is a brief explanation of the fields at the time of registration:
-
Prefixes: It is possible to enter IPv4 and IPv6 prefixes as needed by the environment. Specific prefixes can be used, such as /26 for CDN, /24 for CGNAT, /30 for Servers, and /32 for Critical Clients. These are just common examples and don't represent a fixed rule.
-
Description: Important field to facilitate identification and organization, allowing to describe the purpose or destination of that prefix.
-
Threshold: It is the set of rules where the limits for the associated prefixes are defined. Only existing thresholds will be available for selection. The creation of new thresholds must be done beforehand, before the prefix is registered.
-
AS-PATH: It is a BGP attribute that indicates the sequence of ASNs (Autonomous Systems) that a route must travel to reach its destination. It helps avoid loops, choose better paths, and enforce routing policies. If your environment's BGP doesn't use AS-PATH in policies, you don't need to register it in prefixes or anti-DDoS actions.
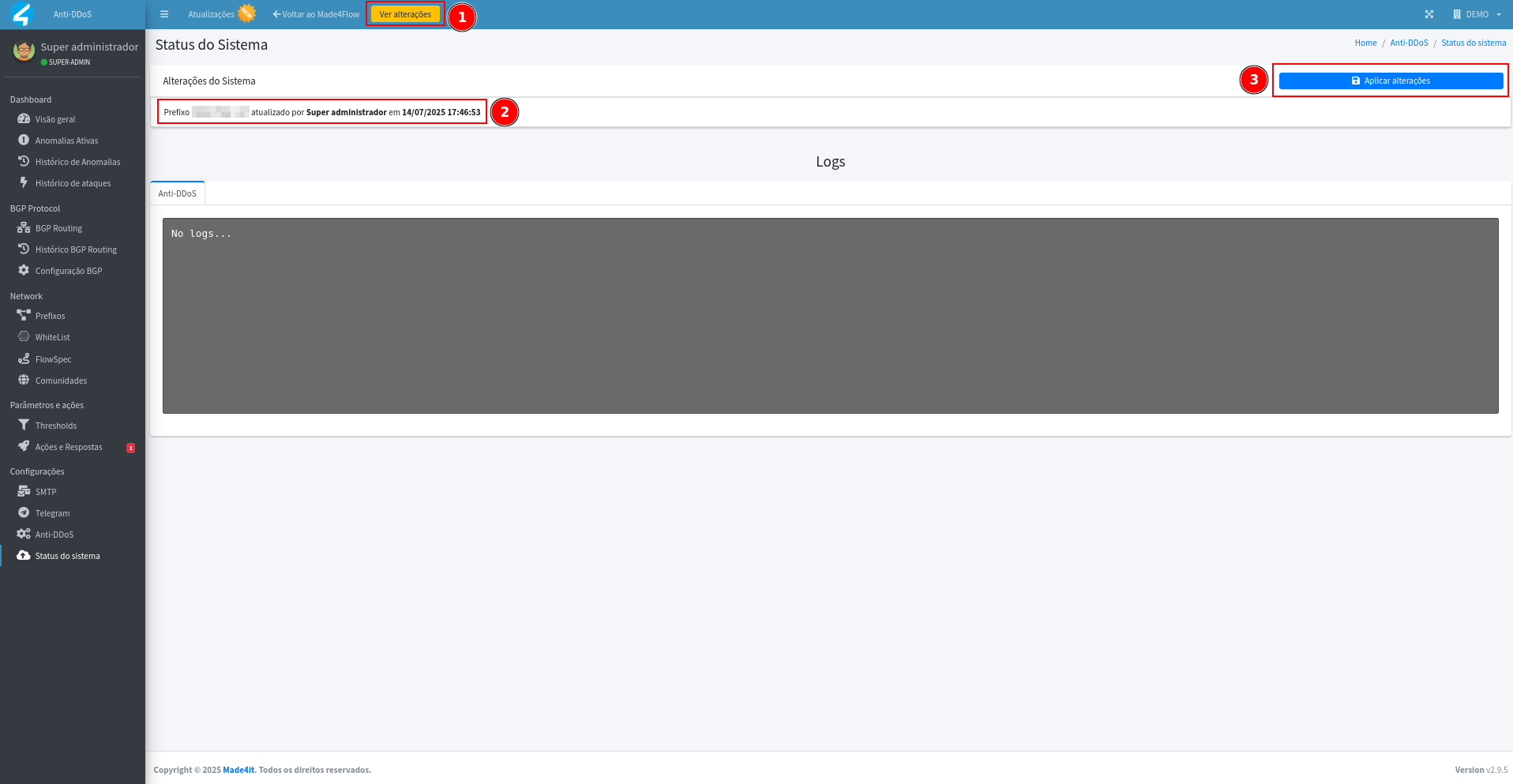
¶ Applying changes
After creating and saving the prefixes, you must apply the changes:
- Click See changes (yellow button).
- Click Apply changes.
¶ Final Thoughts
Organizing prefixes by threshold allows for more granular and efficient control in the detection and mitigation of anomalies. This way, you can apply specific actions according to the critical nature and traffic profile of each IP group, improving anti-DDoS accuracy and reducing false positives.