¶ BGP Communities Examples for Blackhole, Mitigation, and FlowSpec
¶ Purpose of this Wiki
Present definitions, examples, and how to register BGP communities used in announcements for mitigation, blackhole, and FlowSpec.
¶ BGP Community Types and Applications
Before applying any policy via BGP communities, it is important to understand the types, general concepts, and most common uses.
¶ Blackhole
Definition:
Send the prefix to a null0 route, discarding all traffic destined for it. This technique is used to mitigate the impact of volumetric DDoS attacks on specific IPs.
Example of Community used:
00000:666
Commonly used prefixes:
/32for IPv4/128for IPv6
Important: It is not recommended to advertise aggregated subnets for blackhole, as this can affect other legitimate services in the same block.
Advantage: quick mitigation for an ip under attack.
Disadvantage: makes the ip inaccessible to legitimate traffic.
¶ Mitigation
Definition:
Redirects prefix traffic to specialized mitigation systems (scrubbing centers), where traffic is analyzed and filtered before being forwarded to the destination network.
Examples of Communities:
00000:667 # Default mitigation
00000:668 # Mitigation 2 (another profile or type of mitigation)
Recommended Prefixes:
/24for IPv4/48for IPv6
Community choice may depend on the level of aggressiveness or desired route for mitigation.
Advantage: keeps the ip accessible after filtering.
Disadvantage: depends on the availability and capacity of mitigation systems.
¶ Using FlowSpec Templates or Communities
Definition:
BGP FlowSpec allows creating dynamic traffic filtering and control policies based on attributes such as source/destination ip, protocol, port, etc. Actions can be associated with specific BGP communities that indicate what should be done with traffic that matches the rule.
There are ready-made templates that can be used in Anti-DDoS, just access the Templates tab to view:
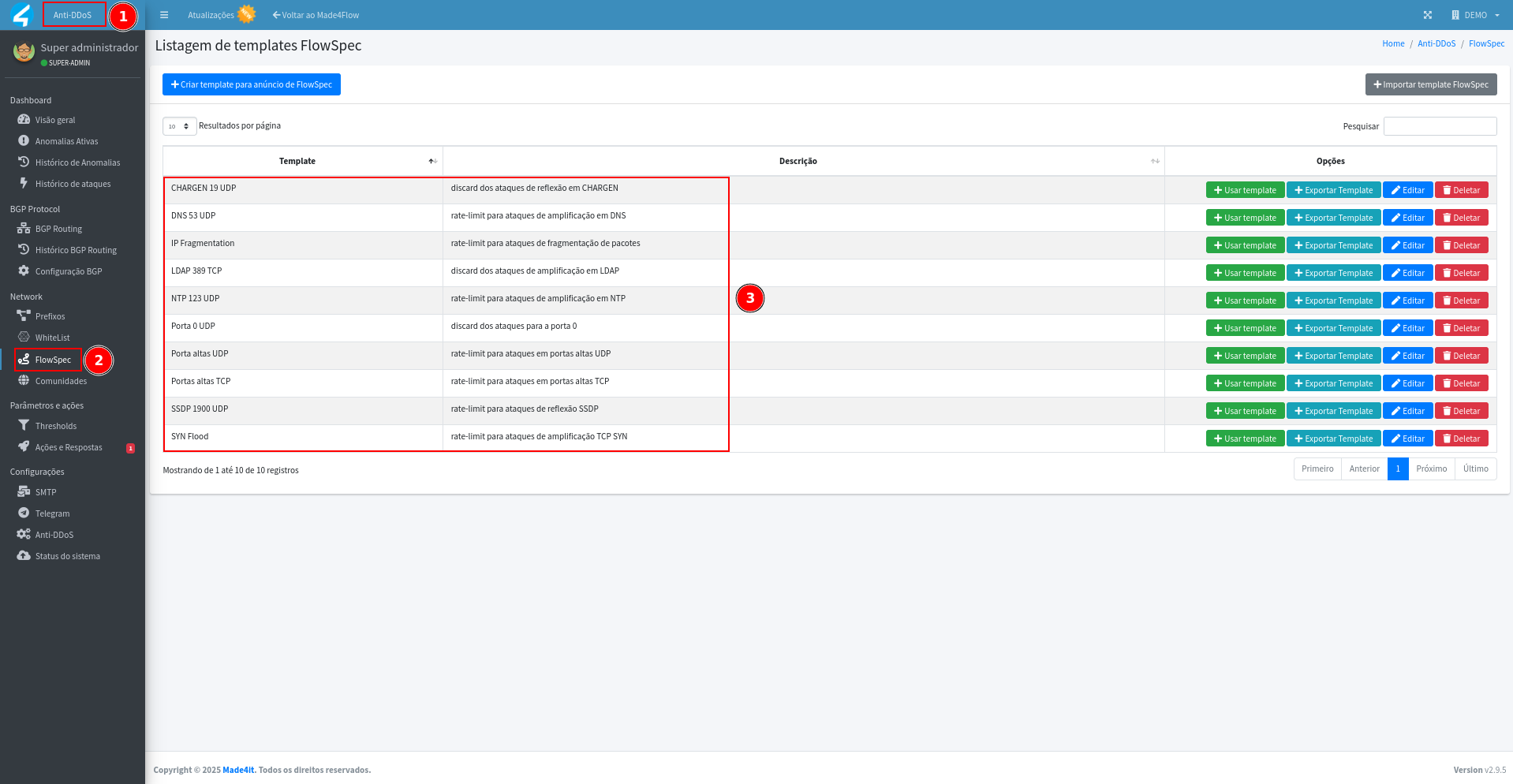
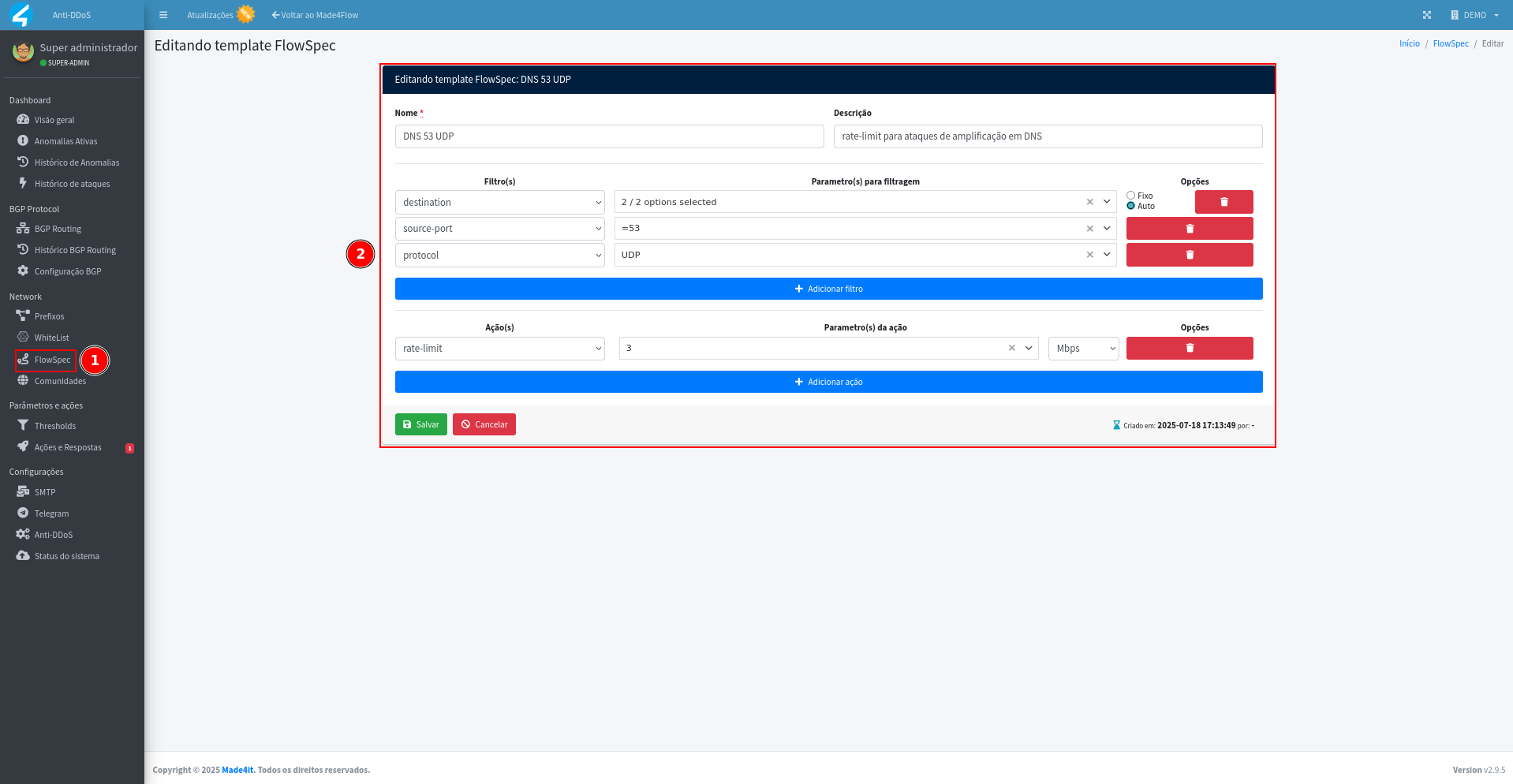
This is an example of a predefined template for rate-limiting DNS 53 UDP:
¶ Main actions and associated FlowSpec communities:
| Community | FlowSpec Action | Description |
|---|---|---|
00000:666 |
deny |
Discards packets (default blocking action) |
00000:777 |
rate-limit |
Limits the traffic (e.g.: 3 Mbps) |
00000:888 |
redirect |
Redirects traffic (honeypot, analysis, etc.) |
The detailed configuration of each FlowSpec rule can be done through predefined or customized templates in Anti-DDoS.
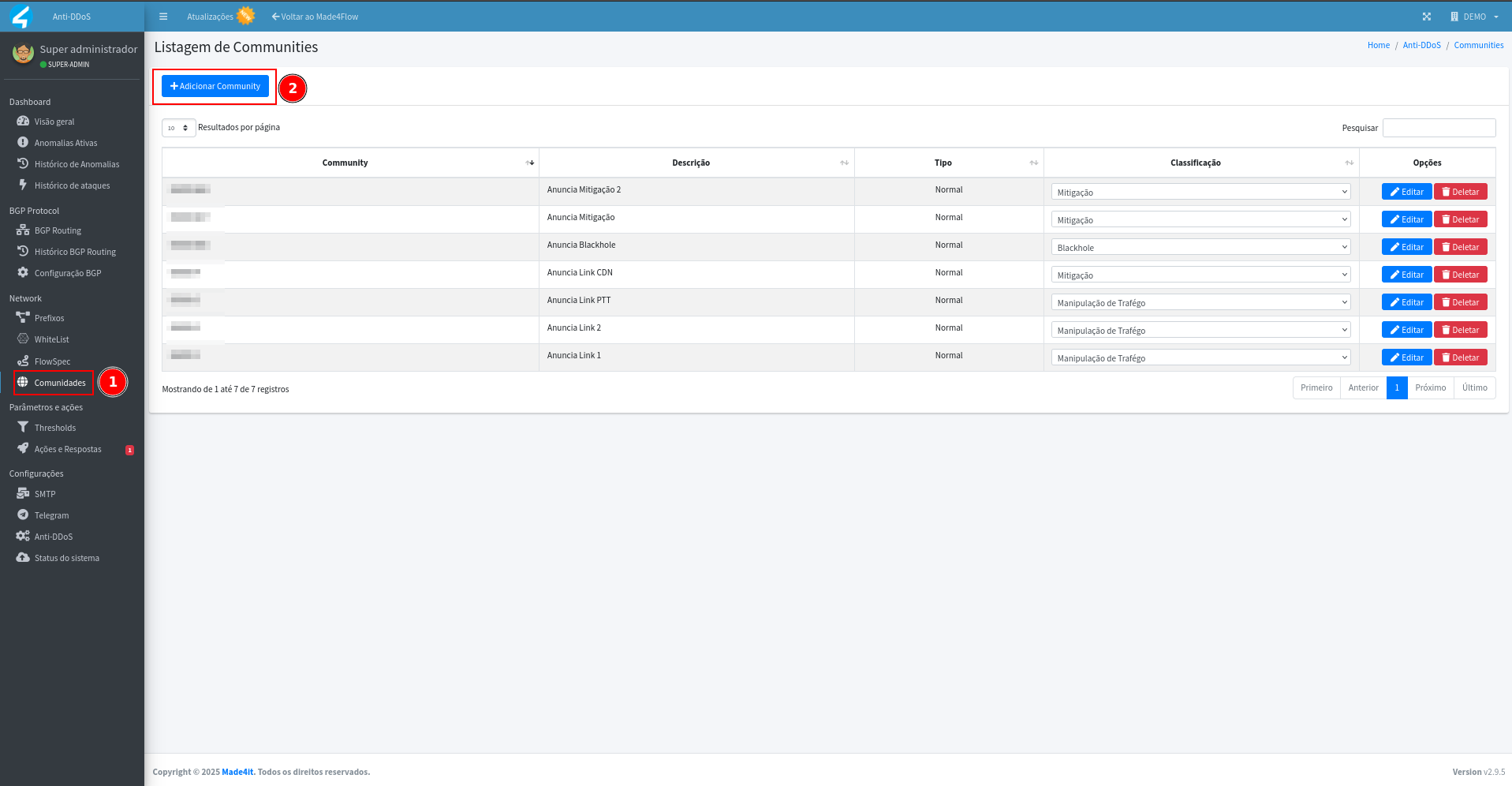
¶ Registration of Communities in Anti-DDoS
In the Communities tab, access Add Community:
Then define the Community, the description, the type, the classification, and save:
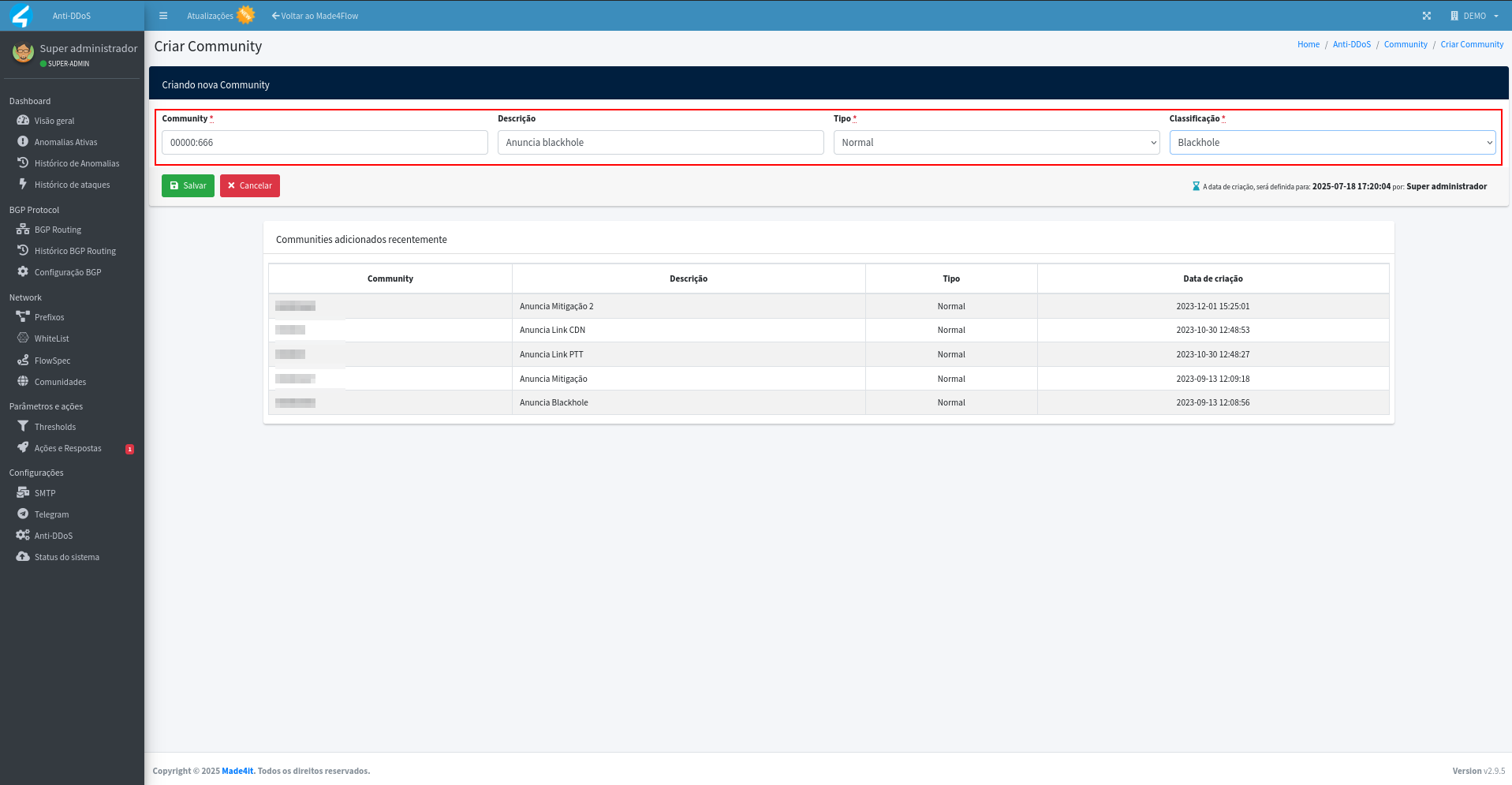
After that, the communities will be available to be associated with Actions and Responses, as well as for manual announcements.
¶ Final Considerations
The application of BGP communities is essential for efficient mitigation of DDoS attacks and for optimizing traffic routing. Understanding the function of each community allows for more precise decision-making and reduces risks such as service unavailability and collateral impacts.
If you have any doubts about the compatibility of communities with your router or provider, it is recommended to consult the official technical documentation or contact technical support.