
¶ What is FlowSpec?
FlowSpec, or Flow Specification, refers to an approach to configuring network traffic policies. It allows a more granular and precise definition of routing and flow control rules, allowing for dynamic adaptation to the different types of DDoS attacks towards our networks.
¶ What is a FlowSpec template for?
The FlowSpec template is a predefined structure that simplifies the process of creating and implementing FlowSpec rules. It works as a standardized model, providing a consistent basis for specific network traffic policy settings. This model can include parameters such as source addresses, destination addresses, protocol, ports, and other relevant characteristics.
As DDoS attacks change, FlowSpec templates provide flexibility to make dynamic adjustments to network traffic policies. This allows an agile response to changes in network conditions, ensuring efficient adaptation to this constant evolution.
¶ Creating a FlowSpec template
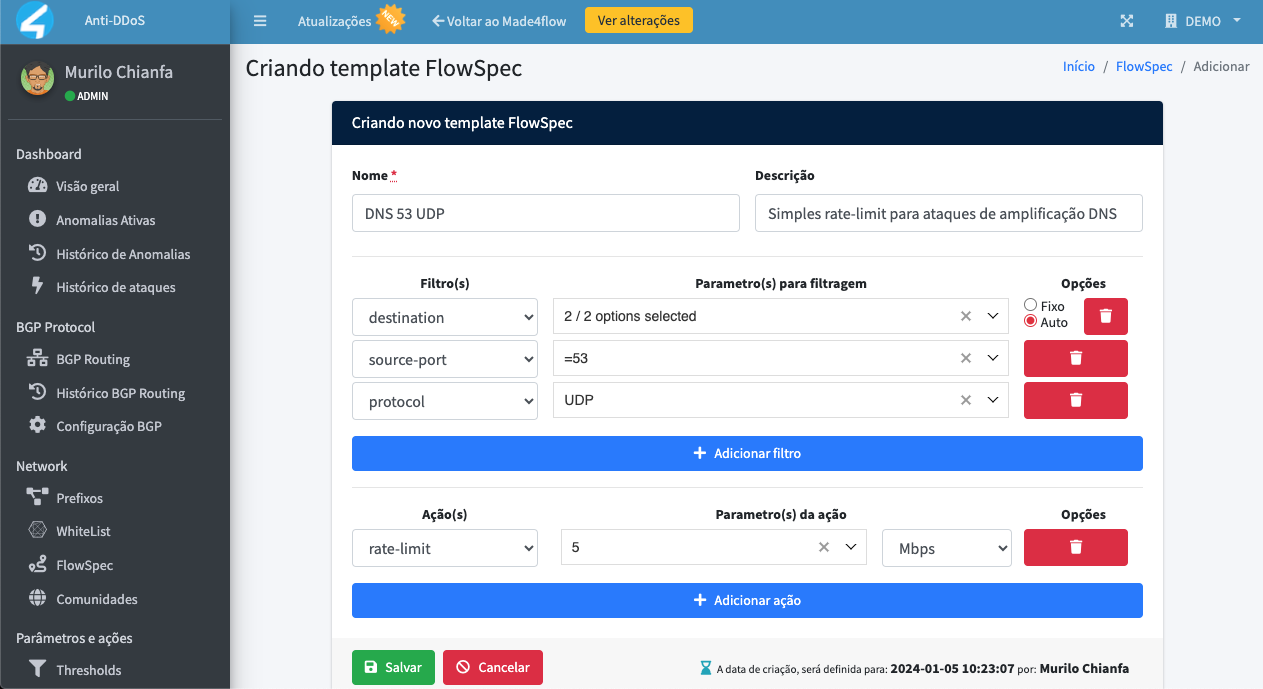
To start, let's create a FlowSpec template to protect against DNS amplification attacks, which pose a significant threat by exploiting vulnerabilities in the DNS protocol to flood targets with excessive traffic.
Unlike RTBH advertisements, in FlowSpec we have the option of using proactive rate-limiting measures, in order not to cut off network traffic completely, but rather to let a few bits pass to try to give a better perception to the target of the attack than simply cutting it off completely from the internet.
To specifically mitigate these types of attacks, which have as their standard characteristic, the sending of many packets with origin port 53 using the UDP protocol, we will develop a FlowSpec template that goes hand in hand with these characteristics, adding a rate-limit slightly higher than usual for everyday use:
¶ Adding FlowSpec actions
Now that we have the FlowSpec template, let's create some automatic actions and responses for new anomalies detected with this signature: